最新下载
热门教程
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
实例演示站点安全漏洞分析与建议报告
时间:2022-06-24 15:47:04 编辑:袖梨 来源:一聚教程网
前两天应上司的要求对公司某频道做了日志的分析
备注:xxx代表某域名或某信息
一、日志记录分析
漏洞1:文件上传漏洞危险等级:非常严重
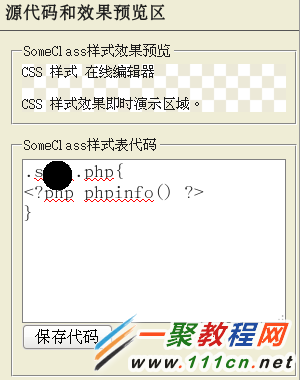
通过日志分析,发现黑客在2014年2月22日用http://xxx/css_edit/css.php(后来更改为cssx.php)文件上传漏洞,获取webshell权限,并且在服务器上植入木马程序。
黑客分别在2014年2月27日和2014年3月3日通过木马程序远程操作,植入恶意“时时彩templates_c/templates.php”。
漏洞2:数据库文件暴露危险等级:严重
http://xxx/configuration.php1205
http://xxx/configuration.php140304等
运维人员不正确备份数据文件
下面具体日志记录
| 代码如下 | 复制代码 |
1.80.76.136 - - [22/Feb/2014:16:01:26 +0800] "GET /css_edit/css.php HTTP/1.1" 200 45841 1.80.76.136 - - [22/Feb/2014:16:01:43 +0800] "POST /css_edit/css.php HTTP/1.1" 200 45969 1.80.76.136 - - [22/Feb/2014:16:03:30 +0800] "POST /css_edit/css.php HTTP/1.1" 200 45943 1.80.76.136 - - [22/Feb/2014:16:06:43 +0800] "POST /css_edit/css.php HTTP/1.1" 200 45958 1.80.76.136 - - [22/Feb/2014:16:06:47 +0800] "GET /css_edit/css.php HTTP/1.1" 200 45841 1.80.76.136 - - [22/Feb/2014:16:09:41 +0800] "GET /css_edit/css.php HTTP/1.1" 404 214 1.80.76.136 - - [22/Feb/2014:19:17:11 +0800] "GET /css_edit/css-bak/css.php HTTP/1.1" 500 - 1.80.76.136 - - [22/Feb/2014:19:17:44 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 458 1.80.76.136 - - [22/Feb/2014:19:17:50 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 3463 222.90.106.49 - - [27/Feb/2014:19:55:17 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 3297 222.90.106.49 - - [27/Feb/2014:19:55:25 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 115 222.90.106.49 - - [27/Feb/2014:19:55:27 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 734 222.90.106.49 - - [27/Feb/2014:19:55:42 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 1370 222.90.106.49 - - [27/Feb/2014:19:55:54 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 4123 222.90.106.49 - - [27/Feb/2014:19:56:07 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 4187 222.90.106.49 - - [27/Feb/2014:19:56:15 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 996 222.90.106.49 - - [27/Feb/2014:19:56:17 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 1088 222.90.106.49 - - [27/Feb/2014:19:56:25 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 830 222.90.106.49 - - [27/Feb/2014:19:56:51 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 33488 222.90.106.49 - - [27/Feb/2014:19:57:11 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 226 222.90.106.49 - - [27/Feb/2014:19:57:12 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 73 222.90.106.49 - - [27/Feb/2014:19:57:17 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 273 222.90.106.49 - - [27/Feb/2014:19:57:20 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 73 1.86.179.21 - - [03/Mar/2014:13:26:43 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 47454 1.86.179.21 - - [03/Mar/2014:13:27:08 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 43 1.86.179.21 - - [03/Mar/2014:13:27:21 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 7 1.86.179.21 - - [03/Mar/2014:13:27:21 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 500 161 1.86.179.21 - - [03/Mar/2014:13:27:38 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 500 161 1.86.179.21 - - [03/Mar/2014:13:28:57 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 500 161 1.86.179.21 - - [03/Mar/2014:13:29:02 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 500 161 1.86.179.21 - - [03/Mar/2014:13:30:28 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 - 1.86.179.21 - - [03/Mar/2014:13:30:32 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 - 1.86.179.21 - - [03/Mar/2014:13:30:35 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 - 1.86.179.21 - - [03/Mar/2014:13:30:47 +0800] "POST /css_edit/css-bak/css.php?2=assert HTTP/1.1" 200 6 |
|
入侵点:http://xxx/css_edit/cssx.php
生成文件地址:http://xxx/css_edit/s.php
xxx在2014年3月13加强安全策略禁止大部分php危险函数及限制站点目录,但是此严重漏洞尚未修复,还可以利用。
三、尝试通过黑客留下的木马程序远程连接服务器
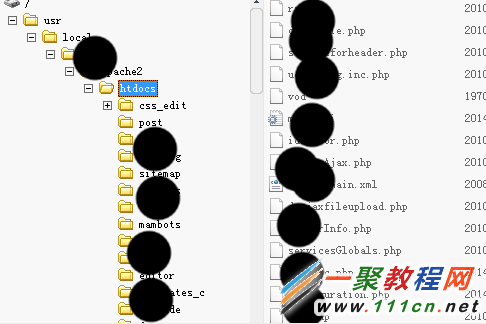
获取文件管理权限截图
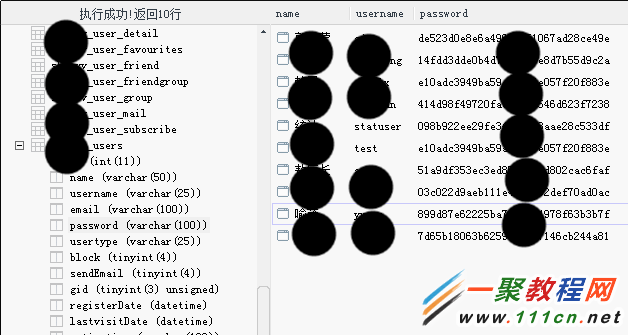
获取数据库权限截图
并尝试了破解md5
成功破解,密码非常简单
后台地址:http://xxx/administrator
案例:用户名gjy 密码gjy123
四、数据库数据及日志分析
百度收录频道“时时彩”:目前对数据库数据及日志,检索暂无发现“时时彩”恶意数据。
五、安全建议:
1、备份数据,对数据再次过滤一下是存留下恶意代码,对比所有文件找出所有木马或者重新装应用。
2、修复上文所说的漏洞。
3、有可能黑客通过webshell权限提权获取了系统权限,修改系统管理密码。
4、应用后台管理员密码尽量超8位(数字字符特殊字符组成)。
5、备份文件不能备份的站点内
相关文章
- 《弓箭传说2》新手玩法介绍 01-16
- 《地下城与勇士:起源》断桥烟雨多买多送活动内容一览 01-16
- 《差不多高手》醉拳龙技能特点分享 01-16
- 《鬼谷八荒》毕方尾羽解除限制道具推荐 01-16
- 《地下城与勇士:起源》阿拉德首次迎新春活动内容一览 01-16
- 《差不多高手》情圣技能特点分享 01-16